Draw.io Vulnerability
Draw.io Vulnerability - From today through december 20th 2023, all researchers will earn 6.25x our normal bounty rates when wordfence handles responsible disclosure for our holiday bug extravaganza! These cves are retrieved based on exact matches on listed software, hardware, and vendor information (cpe data) as well as a keyword search to ensure the newest vulnerabilities with no officially listed software information are still displayed. Improper input validation/sanitization of a color field leads to xss. Updates gliffy submodule for new shapes mappings. Threat modelling, especially in it, is becoming more common. Register as a researcher and submit your vulnerabilities today! This could allow a malicious actor to inject malicious scripts, such as redirects, advertisements, and other html payloads into your website which will be executed when guests visit your site. Web this page lists vulnerability statistics for draw » draw.io diagrams » 2.7.0 for confluence. An issue was discovered in mxgraph through 4.0.0, related to the draw.io diagrams plugin before 8.3.14 for confluence and other products. This can lead to a leak of sensitive information. Register as a researcher and submit your vulnerabilities today! The attack is a stored xss, please contact support if you would like more details. This page lists vulnerability statistics for all versions of draw » draw.io diagrams. Improper input validation/sanitization of a color field leads to xss. T0mwz mentioned this issue on dec 15, 2021. An attacker can make a request as the server and read its contents. The cybersecurity and infrastructure security agency (cisa) has released a summary of the most recent vulnerabilities. Severity cvss version 3.x cvss version 2.0 Web updates draw.io editor to 20.2.1. Works with github, gitlab and dropbox for visual documentation in distributed teams. Improper input validation/sanitization of a color field leads to xss. An attacker can make a request as the server and read its contents. Web description exposure of sensitive information to an unauthorized actor in github repository jgraph/drawio prior to 18.0.7. This is associated with javascript/examples/grapheditor/www/js/dialogs.js. From today through december 20th 2023, all researchers will earn 6.25x our normal bounty rates. An issue was discovered in mxgraph through 4.0.0, related to the draw.io diagrams plugin before 8.3.14 for confluence and other products. These cves are retrieved based on exact matches on listed software, hardware, and vendor information (cpe data) as well as a keyword search to ensure the newest vulnerabilities with no officially listed software information are still displayed. Web analysing. Severity cvss version 3.x cvss version 2.0 cvss 3.x severity and metrics: Web certain versions of draw.io from diagrams contain the following vulnerability: You can view versions of this product or security vulnerabilities of draw draw.io diagrams. Threat modelling, especially in it, is becoming more common. The cybersecurity and infrastructure security agency (cisa) has released a summary of the most. Web confluence is a collaboration software for capturing (internal) documentation and supports direct integration with many other systems such as google drive, draw.io. An attacker can make a request as the server and read its contents. This could allow a malicious actor to inject malicious scripts, such as redirects, advertisements, and other html payloads into your website which will be. This is associated with javascript/examples/grapheditor/www/js/dialogs.js. Web resecured.io discovered and reported this cross site scripting (xss) vulnerability in wordpress drawit (draw.io) plugin. The cybersecurity and infrastructure security agency (cisa) has released a summary of the most recent vulnerabilities. In the last few days, cybercriminals have been. This is associated with javascript/examples/grapheditor/www/js/dialogs.js. Web resecured.io discovered and reported this cross site scripting (xss) vulnerability in wordpress drawit (draw.io) plugin. Vulnerability statistics provide a quick overview for security vulnerabilities of draw » draw.io diagrams » version 2.7.0 for confluence. This page lists vulnerability statistics for all versions of draw » draw.io diagrams. Register as a researcher and submit your vulnerabilities today! This is associated. Although the latest vulnerability summary by cisa has been released for the week of december 4, it covers the period from december 1 to december 9, 2023 based on the vulnerability publish dates. An attacker can make a request as the server and read its contents. Web analysing vulnerabilities with threat modelling using draw.io. From today through december 20th 2023,. This is associated with javascript/examples/grapheditor/www/js/dialogs.js. Web certain versions of draw.io from diagrams contain the following vulnerability: An issue was discovered in mxgraph through 4.0.0, related to the draw.io diagrams plugin before 8.3.14 for confluence and other products. Davidjgraph closed this as completed on dec 14, 2021. This can lead to a leak of sensitive information. Web this page lists vulnerability statistics for draw » draw.io diagrams » 2.7.0 for confluence. This page lists vulnerability statistics for all versions of draw » draw.io diagrams. Moves name conflict check to avoid possible db writes when returning 409. You can view versions of this product or security vulnerabilities of draw draw.io diagrams. Web we will release details of the vulnerability after a grace period, if you wish to discuss details with us please contact support in the normal way, support@draw.io ; Vulnerability statistics provide a quick overview for security vulnerabilities of draw » draw.io diagrams » version 2.7.0 for confluence. Given the nature of the issue, if you are not in maintenance to upgrade to 7.0.1, email support@draw.io and we will issue you a free license to upgrade. Register as a researcher and submit your vulnerabilities today! Improper input validation/sanitization of a color field leads to xss. Severity cvss version 3.x cvss version 2.0 cvss 3.x severity and metrics: These cves are retrieved based on exact matches on listed software, hardware, and vendor information (cpe data) as well as a keyword search to ensure the newest vulnerabilities with no officially listed software information are still displayed. The cybersecurity and infrastructure security agency (cisa) has released a summary of the most recent vulnerabilities. Severity cvss version 3.x cvss version 2.0 cvss 3.x severity and metrics: Web drawit (draw.io) plugin claim vdp developer n/a current version n/a installations n/a last updated n/a vulnerability history 1 present 0 patched cross site scripting (xss) vulnerability <= 1.1.3 6.5 16 november, 2023 This is associated with javascript/examples/grapheditor/www/js/dialogs.js. Vulnerability statistics provide a quick overview for security vulnerabilities of draw.io diagrams.
DRAWIO File What is a .drawio file and how do I open it?

Draw Io Diagrams For Everyone Everywhere Draw Io Gambaran

How to use the draw.io Template Manager to work more efficiently with

Tenable.io Vulnerability Management Solution Tenable™
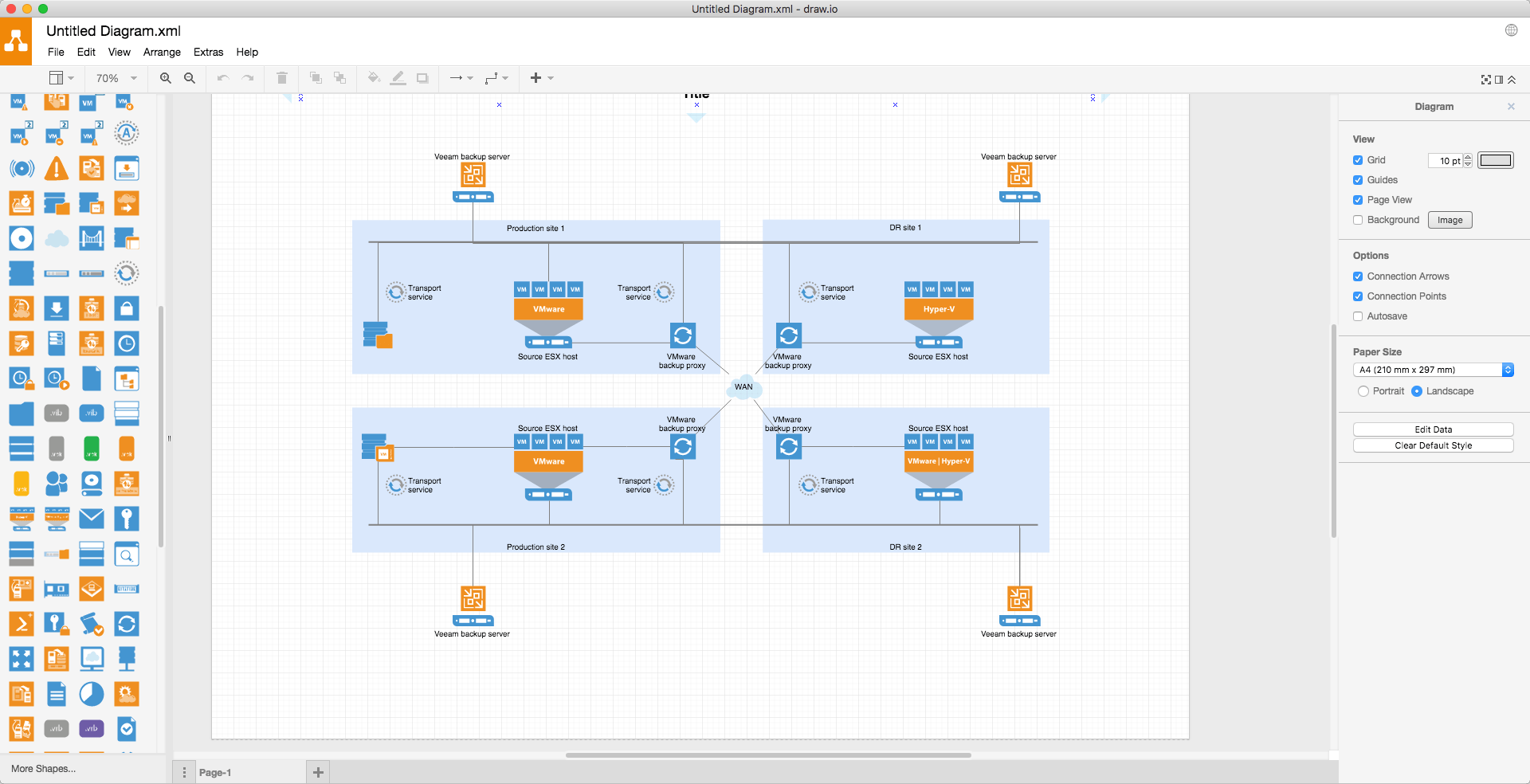
Draw. io The best technical drawing tool, free and online, has now
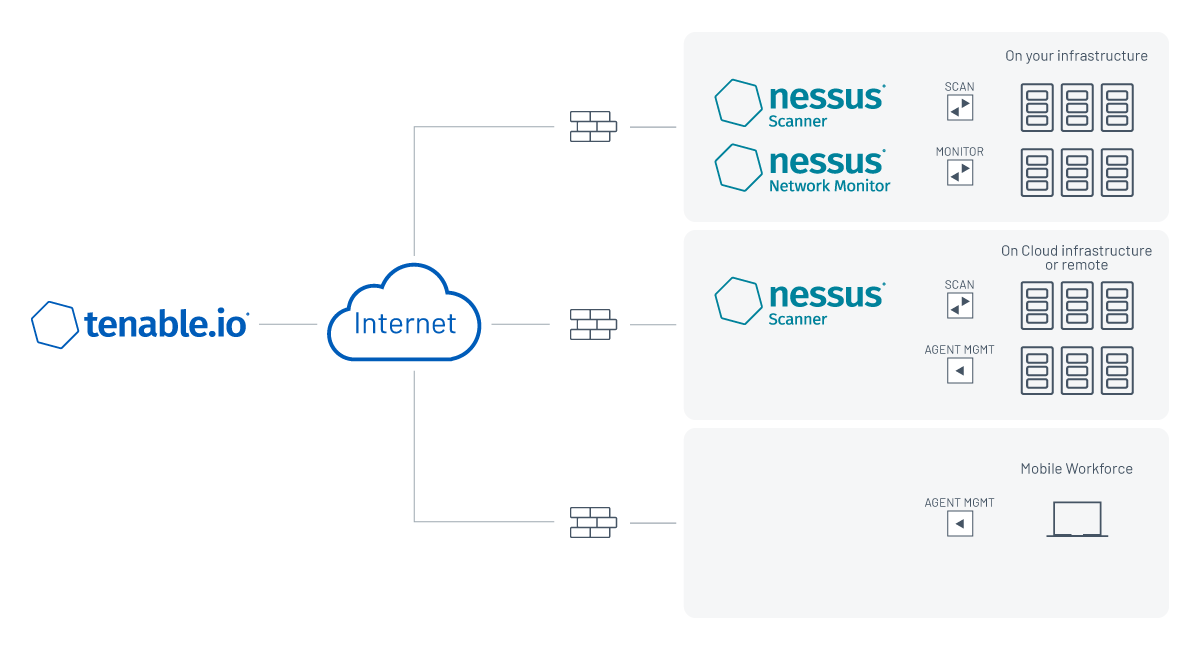
Tenable Vulnerability Management Tenable.IO Tips and Tricks with Best
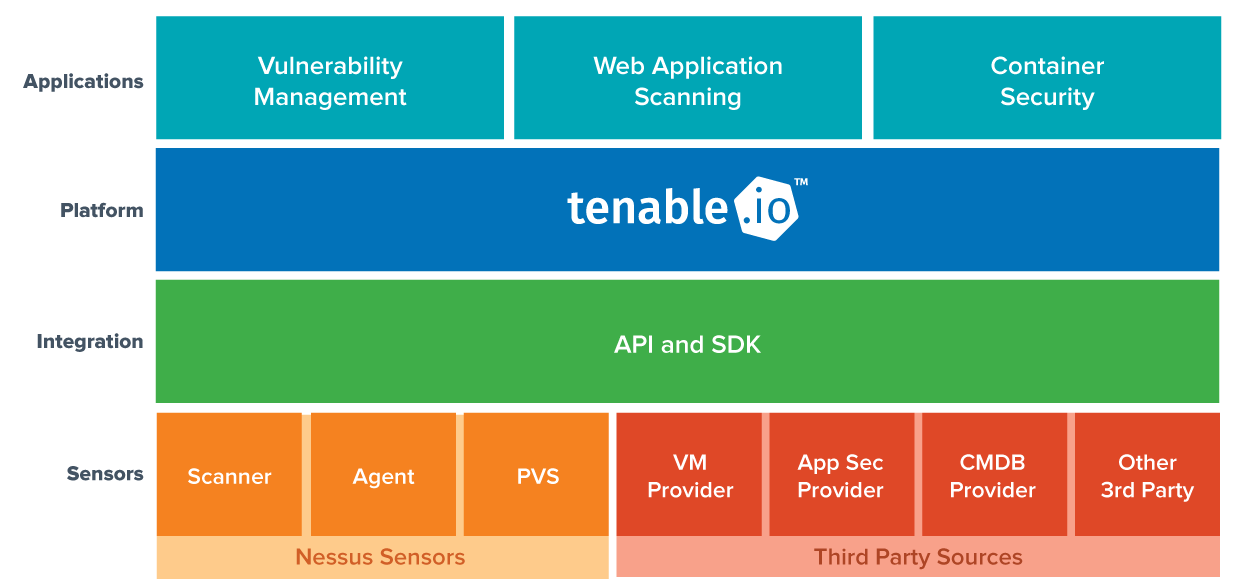
Transforming Vulnerability Management Introducing Tenable.io LaptrinhX
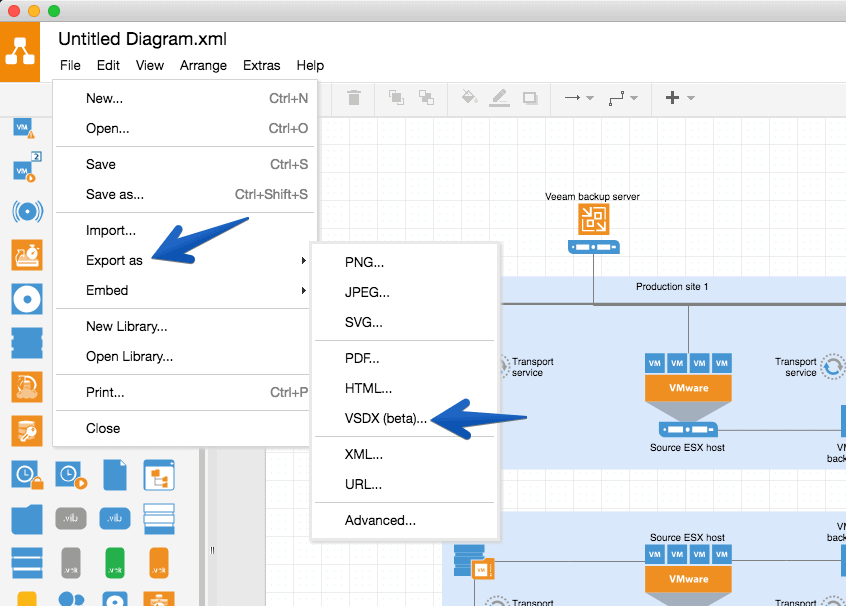
Draw. io The best technical drawing tool, free and online, has now
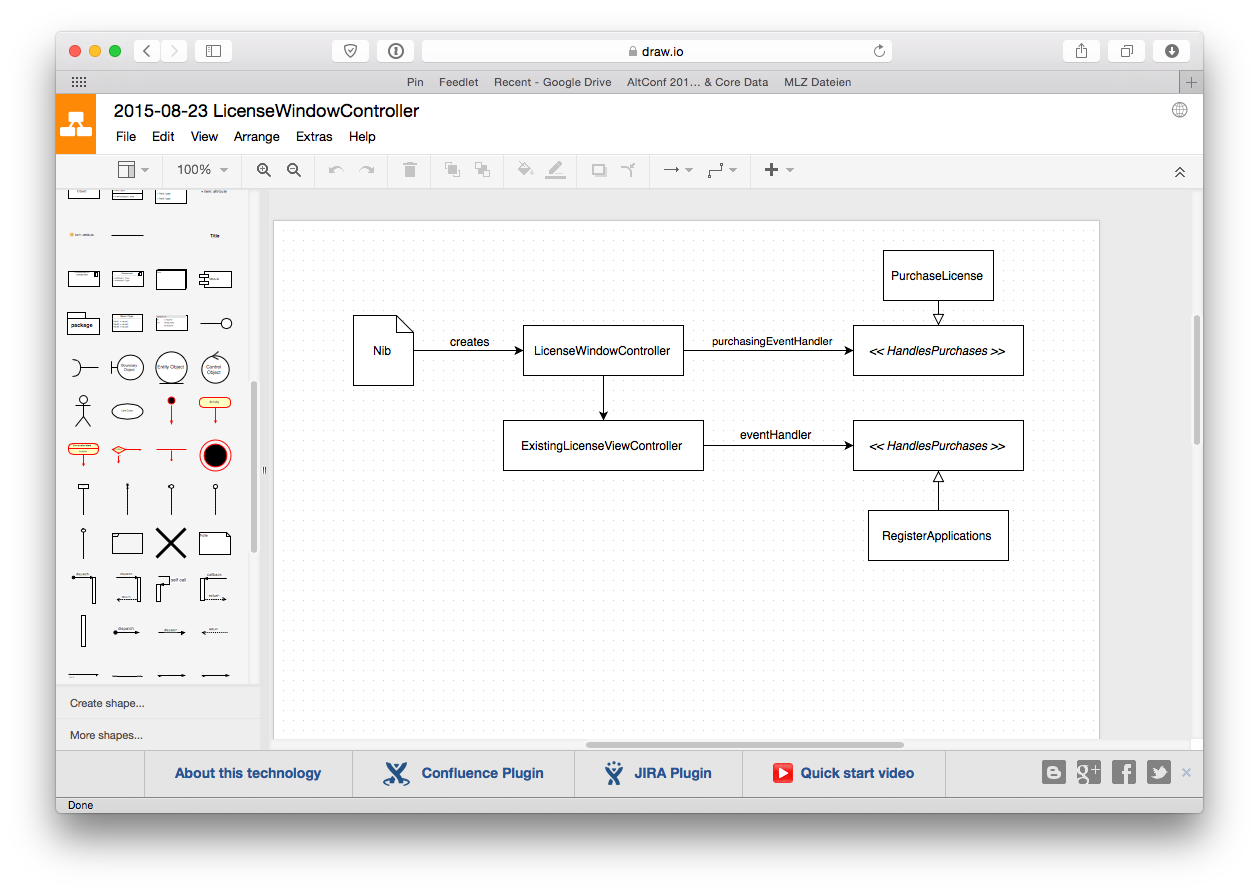
Create UML Diagrams Quickly with Draw.io • Christian Tietze
Create diagrams using draw.io GROWI Docs
Vulnerability Statistics Provide A Quick Overview For Security Vulnerabilities Of Draw.io.
T0Mwz Opened This Issue On Dec 14, 2021 · 1 Comment.
An Attacker Can Make A Request As The Server And Read Its Contents.
Web Certain Versions Of Draw.io From Diagrams Contain The Following Vulnerability:
Related Post: