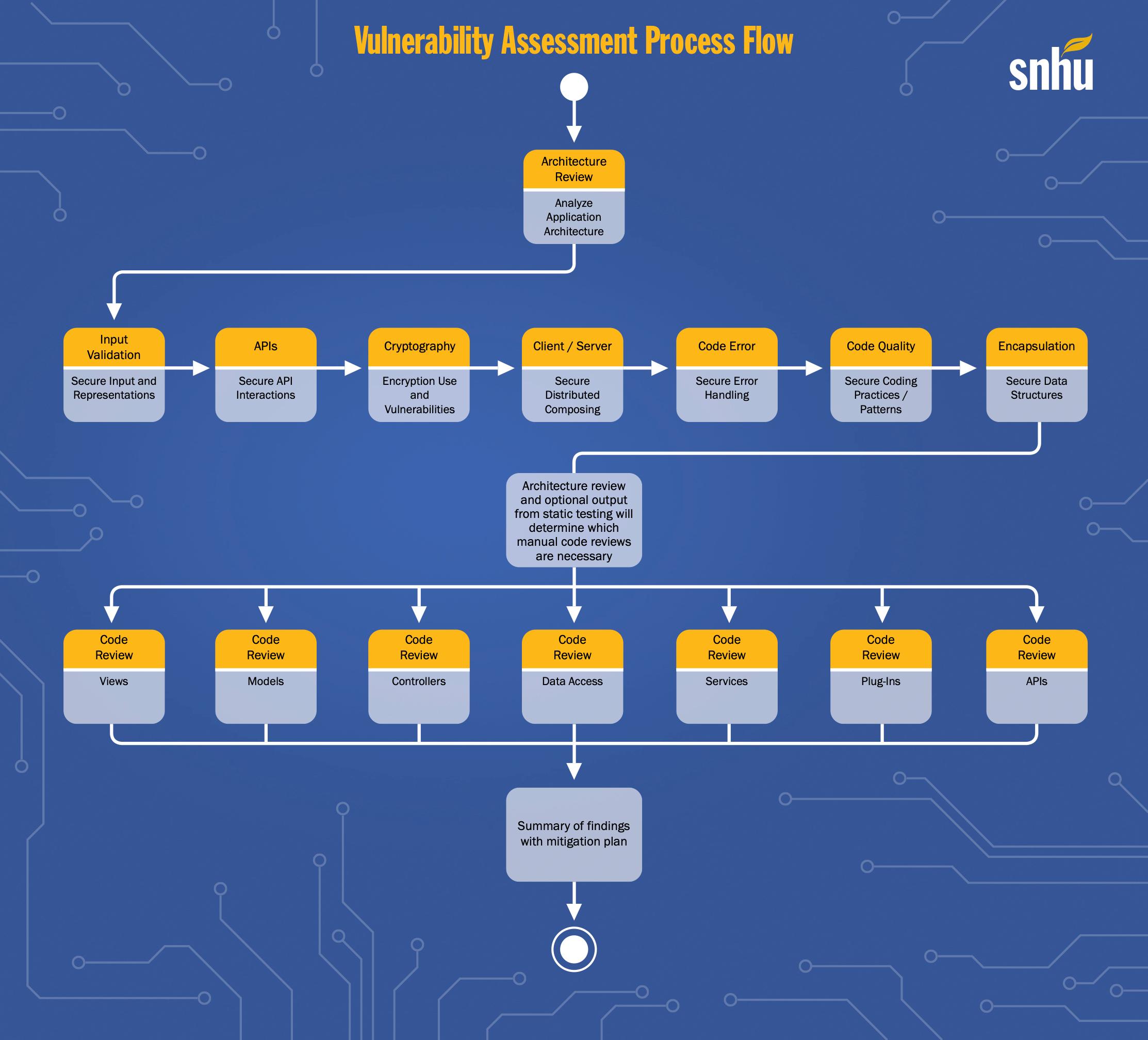
Vulnerability Management Process Flow Chart
Vulnerability Management Process Flow Chart - This is the first stage in the vulnerability management process diagram. Here's how they can benefit you: Web for instance, 1.1 scope influences multiple processes: Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within an organization. Determine scope of the program. Assessment is the first stage of the cycle. How we set up our tools for vulnerability testing, how we group our assets for scans and reporting, how we prioritize remediation, what metrics we would use in our reports, what exceptions from remediation are acceptable and what are not. Web in cybersecurity, vulnerability management is the process of identifying, analyzing, and managing vulnerabilities within an operating environment in order to keep your organization's systems, networks, and enterprise applications safe from cyberattacks and data breaches. The process areas described include • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability If you find conflicting information please raise it to the attention of the security team. At the heart of a typical vulnerability management tool is a vulnerability scanner. Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. Web for example, the task “scope” feeds into multiple processes: Here's how they can benefit you: ★ “vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities”. This is the first stage in the vulnerability management process diagram. Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. Create and refine policy and slas. Web the vulnerability management process is a continuous process for discovering, prioritizing, and resolving. If you find conflicting information please raise it to the attention of the security team. Web there are five stages in the vulnerability management process: The process areas described include • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability ★ “vulnerability management is the cyclical practice of identifying, classifying,. Finding vulnerabilities through scanning and testing, prioritising, fixing, and monitoring vulnerabilities. This is the first stage in the vulnerability management process diagram. Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. The scan consists of four stages: If you find conflicting information please raise it to the attention of the security team. Finding vulnerabilities through scanning and testing, prioritising, fixing, and monitoring vulnerabilities. This document details how to execute the vulnerability management process as documented in our vulnerability management policy. Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. ★ “vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities”. Organizations must identify. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification/scanning phase, the reporting phase, and remediation phase. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within an. Web for instance, 1.1 scope influences multiple processes: The process areas described include • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability The goal of this study is to call attention to something that is often. Web the vulnerability management process is a continuous process for discovering, prioritizing, and. Create and refine policy and slas. At the heart of a typical vulnerability management tool is a vulnerability scanner. Follow these five main steps of the vulnerability management process to strengthen your cybersecurity. Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. Web there are five stages in the vulnerability management process: Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. Organizations must identify vulnerabilities that could negatively impact their systems. Create and refine policy and slas. The goal of this study is to call attention to something that is often. Web in cybersecurity, vulnerability management is the process of identifying, analyzing, and managing vulnerabilities within. Assessment is the first stage of the cycle. Web there are five stages in the vulnerability management process: The scan consists of four stages: This document details how to execute the vulnerability management process as documented in our vulnerability management policy. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability. Organizations must identify vulnerabilities that could negatively impact their systems. Web learn the best practices for implementing a sustainable vulnerability management process, including establishing clear objectives, selecting appropriate tools, maintaining historical data, and acknowledging risks. Vulnerability management is essential to every modern cyber security strategy. If you find conflicting information please raise it to the attention of the security team. Assessment is the first stage of the cycle. Follow these five main steps of the vulnerability management process to strengthen your cybersecurity. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification/scanning phase, the reporting phase, and remediation phase. Web the vulnerability management process is a continuous process for discovering, prioritizing, and resolving security vulnerabilities across an organization’s it infrastructure. Determine scope of the program. The process areas described include • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan • developing a vulnerability discovery capability Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within an organization. At the heart of a typical vulnerability management tool is a vulnerability scanner. ★vulnerability management is an integral part of computer and network security, and must not be confused with a vulnerability assessment. Articles and studies about vm usually focus mainly on the technology aspects of vulnerability scanning. How we set up our tools for vulnerability testing, how we group our assets for scans and reporting, how we prioritize remediation, what metrics we would use in our reports, what exceptions from remediation are acceptable and what are not. ★ “vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities”.Using the Vulnerability Assessment Process Flow
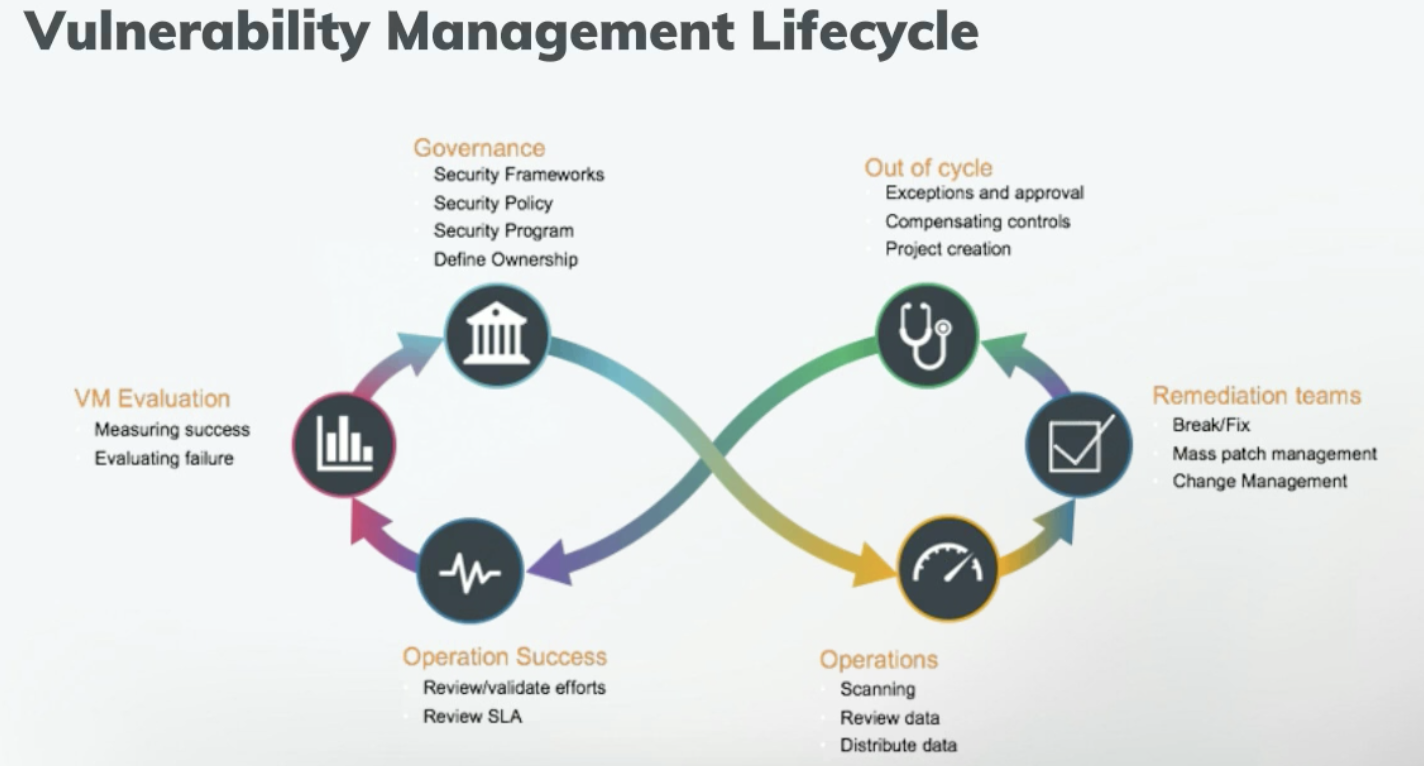
An effective vulnerability management lifecycle Entrepreneur Business

Vulnerability Management Process Flow Chart
Vulnerability Management Process Template
Vulnerability Management Process, what is it? Conviso AppSec
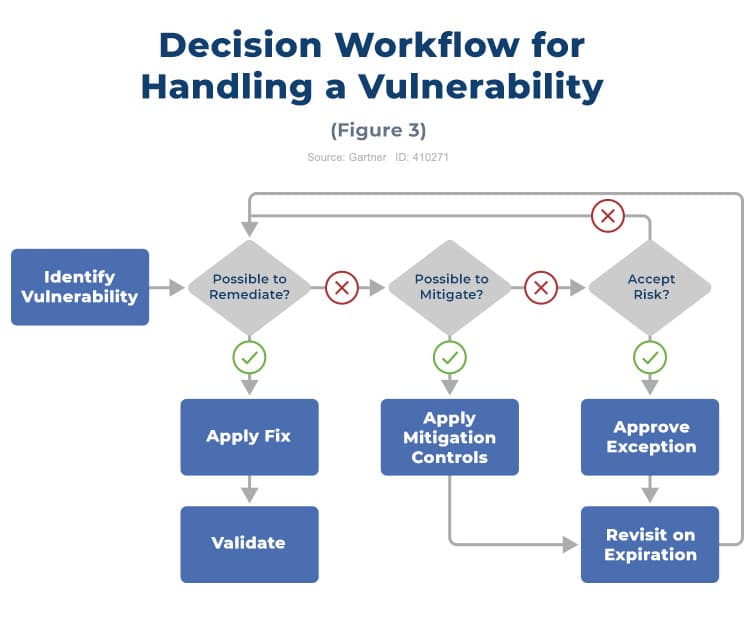
Vulnerability Management Process Flow Chart Rootshell

Vulnerability Management Process Flow Chart Rootshell
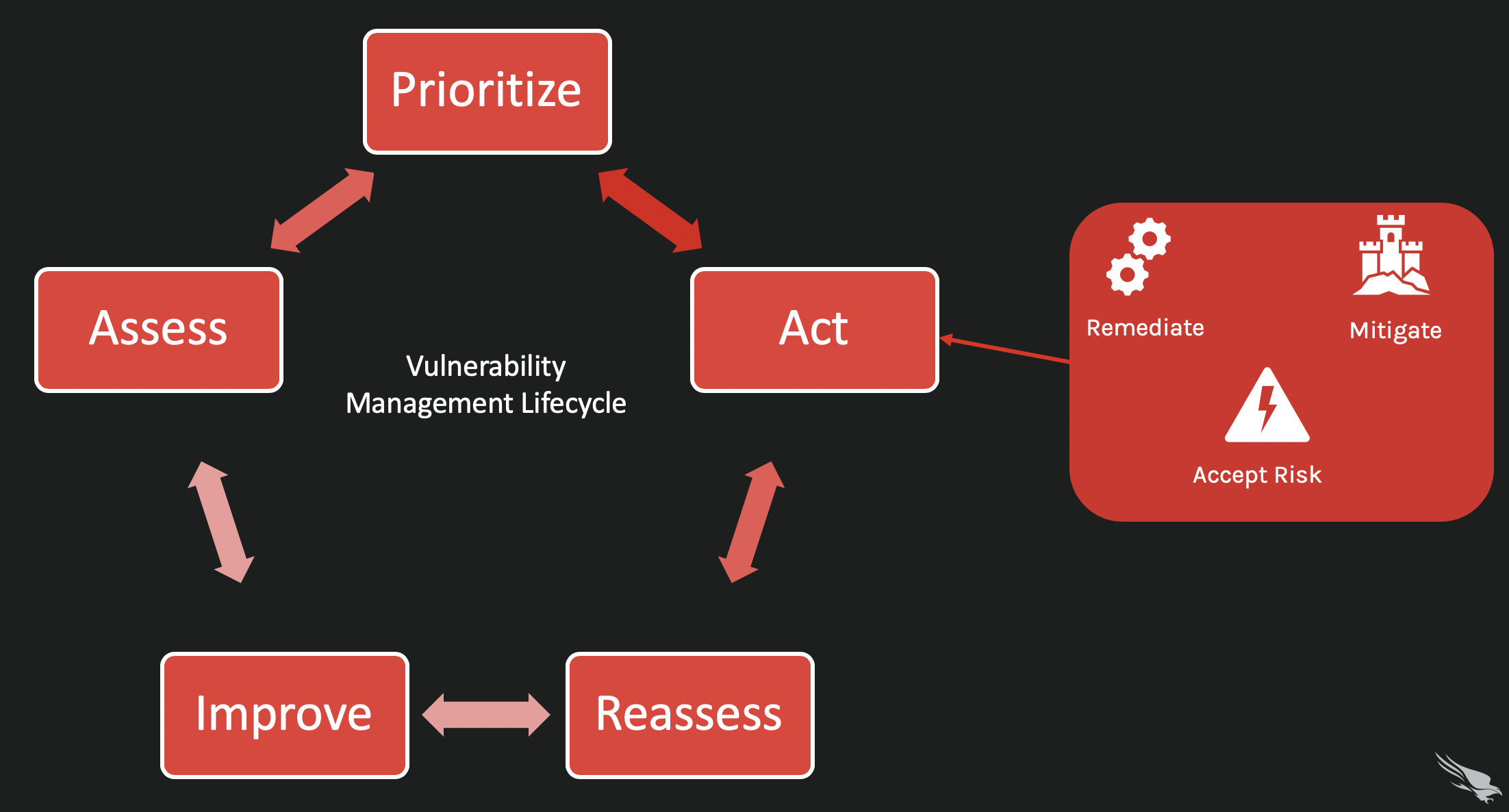
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike

Vulnerability Management Services Optiv

The Vulnerability Management Lifecycle (5 Steps) CrowdStrike
The Policy Document Is The Source Of Truth In Case There Are Any Discrepancies Between The Two Documents.
The Scan Consists Of Four Stages:
Web For Example, The Task “Scope” Feeds Into Multiple Processes:
The Goal Of This Study Is To Call Attention To Something That Is Often.
Related Post: